How to avoid domain theft? Best practices for securing your domains

Is it possible to steal an internet domain? You might be surprised, but yes, it is. This offense is not common, but it does happen. For example, in 2015 a company selling glasses fell victim to such practice. In July 2021, a cybercriminal used a cunning method and stole a domain using the domain aftermarket. We have described the examples in detail in this article and we want them to serve as a warning to domain subscribers.
Are you curious about the methods used by cybercriminals to steal domains and how you can protect yourself against them? Read about it below.
How can cybercriminals steal an internet domain?
An internet domain can be stolen in two ways:
- By changing the domain delegation, i.e. redirecting it to external DNS servers. To do this, it may be sufficient to know the login credentials to the domain administration panel. By changing the delegation, you can intercept e-mail traffic and redirect the domain to a fake website hosted elsewhere.
- By transferring the domain, i.e. moving it to another registrar and, in consequence, completely taking over the domain.
In the case of most registrars, in order to transfer a domain, you'll need:
- Login credentials to the domain administration panel, i.e. the e-mail address or account name and the corresponding password.
- Authinfo code – a string of characters that allows you to transfer a domain, i.e. move it to another registrar. Usually, the code can be obtained after additional authorization, for example after completing an application for a code. There are, however, exceptions for domains that don’t have authinfo codes, such as the British ".uk" extension.
- Login details to the domain subscriber's mailbox, because this is where the authinfo code is usually sent. However, the authinfo code can also be made available directly in the domain administration panel.
In 2015, the domain shadesdaddy.com, which sells luxury glasses, fell victim to such theft. The domain was stolen by Chinese cybercriminals and redirected to another fake website. Eventually, the domain was recovered, but not before the thieves managed to sell hundreds of counterfeit products, which had a negative impact on the company's image.
How to protect your domain from theft – practical tips
1. Pay attention to the domain name of the website you are logging in to
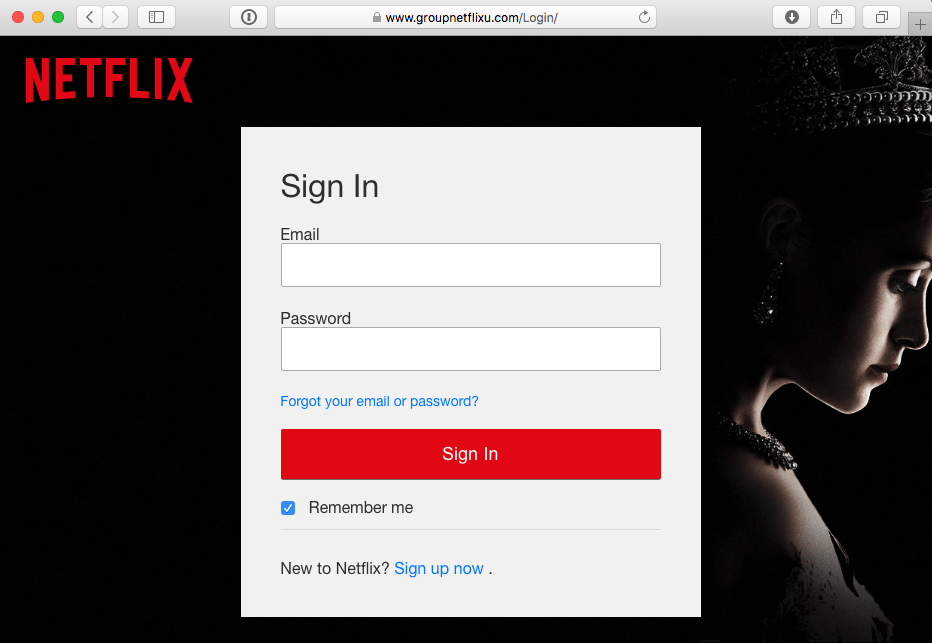
Take a look at the screenshot below. Do you see anything disturbing?
Source: https://isc.sans.edu/diary/Secure+Phishing%3A+Netflix+Phishing+Goes+TLS/23786
It’s the fake URL: “https://www.groupnetflixu.com/Login/” instead of “https://www.netflix.com/Login/”.
The scammer added the word “group” in front of the original name and the letter “u” at the end. He deployed a fake website similar to the Netflix login form at this address.
This is a good example of phishing. This type of scam consists of impersonating an existing website to obtain confidential information and is based on social engineering techniques. The goal is to prompt users to make wrong decisions, manipulate them and convince them to take actions that will result in fraud.
The chances of an attack being successful are influenced, among others, by the quality of the fake portal, the choice of a similar domain name, and the method of encouraging visitors to take further action, for example via a properly titled e-mail with well-thought-out content, quality graphics, and other effective “decoys”. In the case of the Netflix fraud, the scammer used a name that was very similar to the genuine one.
A cybercriminal could send a fake message to potential LetsDomains.com subscribers, for example about a new offer related to our services, from a different domain. The content could include links to a fake domain. The sender's name could be different from the original one, but at the same time look similar enough to be mistaken for the genuine one.
Some people may not notice that the link leads to a fake portal. Of course, the name of the sender would also be different from the original one, but the alphabets around the world are so complex that it’s possible to register an analogous name that looks similar.
Popular ways to spoof domains include adding one or more similar-looking letters to the address, such as ḁ instead of a, which look very alike, but come from different alphabets.
The method involving using a similar-looking letter was, for example, used by scammers who registered the lọt.com (Polish Airlines) domain and published a fake airline ticket sales portal there. The middle letter is “o” with a dot at the bottom, which is a Latin character in the Igbo language.
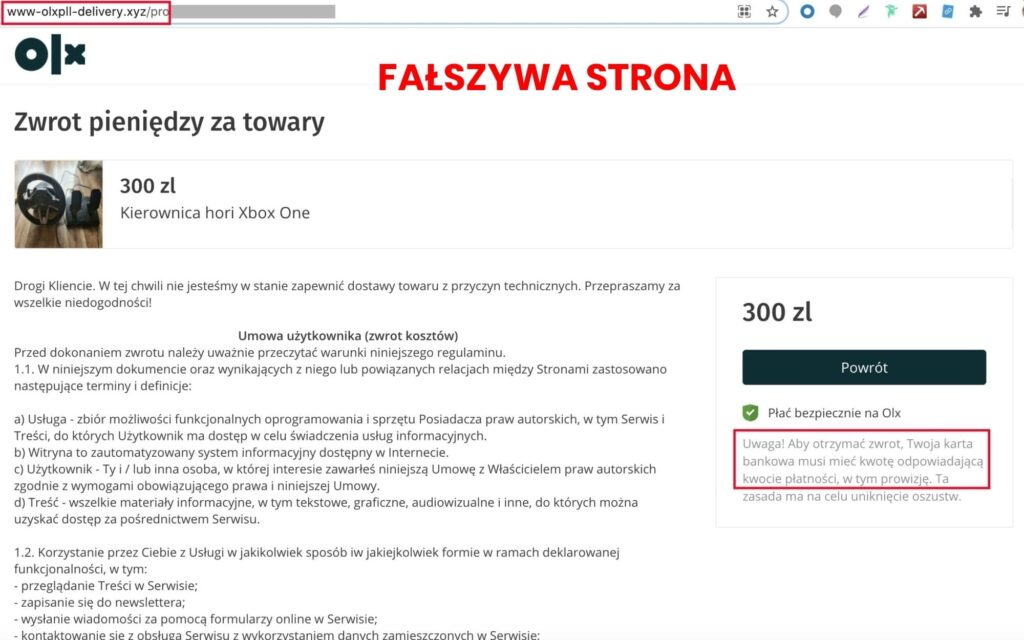
Other methods consist of duplicating letters next to each other or adding words like delivery, shipments, marketplace shipments, 24, shopping, etc. One of the portals that scammers often impersonate is OLX (a popular classified website in Europe). You can read about dishonest methods that caused many people to lose their money on their blogs. Therefore, always look carefully at the website URL as it may save you from a potential scam.
Source: https://blog.olx.pl/2020/06/18/uwaga-na-phishing/
2. Avoid logging into open Wi-Fi networks and using accounts on public devices
Perhaps you have logged in to an open Wi-Fi network, meaning a network where you don’t need a password to sign in. They can be found, for example, at airports or shopping malls. We advise against such connection attempts, in particular, logging into your private accounts, including the domain administration panel. Be aware that a given hotspot may have been created specifically for the purpose of data theft.
When creating a Wi-Fi network, you can easily name it using the name of an airport or a shopping mall. If you log in to a network created by a cybercriminal, they will be able to view information sent between your device and the unencrypted websites you visit, for example, websites not protected with the HTTPS protocol via an SSL certificate. This is because this way thieves become intermediaries between the network and the device.
A similar rule applies to logging into private accounts on public, unknown devices, for example in a library, internet café, or at a photocopying point. Such facilities may use trusted Wi-Fi networks, but may not have complete control over the people who visit them. It’s enough for a cybercriminal to infect a device with undetectable malware, such as a keylogger, which will record the characters typed by the device users.

3. Use different, strong passwords
Using the same password everywhere is certainly a convenient solution, but it’s associated with considerable danger. If your login details get leaked from one website, the cybercriminal will probably attempt to use them elsewhere. Therefore, there is a risk that the thief will log into the other platforms you use via trial and error. Seems unrealistic? Maybe you’ll be convinced by a news piece published by TroyHunt.com (a security-focused blog) that describes a leak of 21 million passwords from 2000 platforms.
If you’re worried that you’ll not be able to remember all these passwords, you can use dedicated software, such as Password Safe, KeyPass, and LastPass, to securely collect and store your credentials. The programs are available for both computers and smartphones.
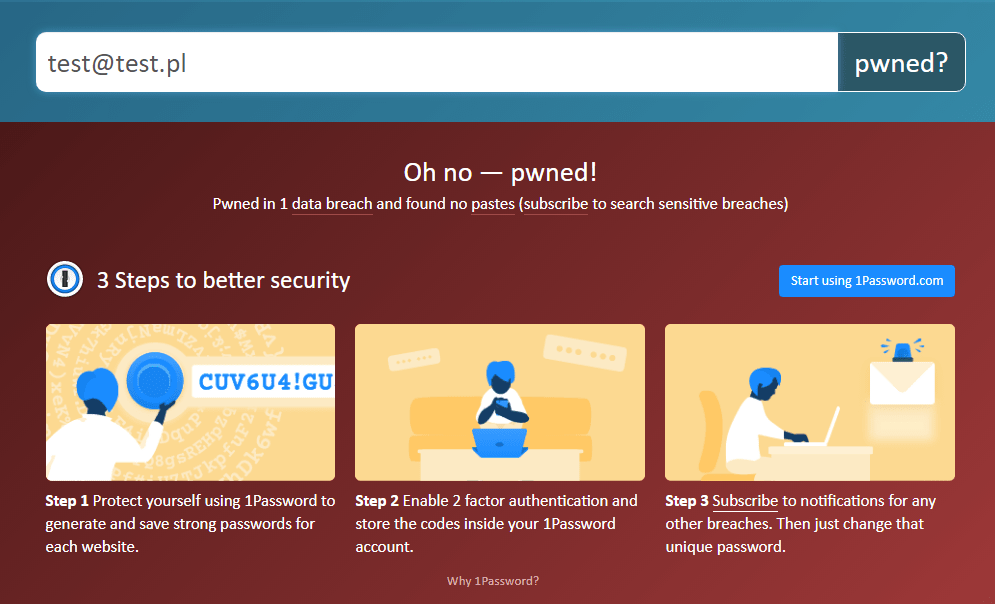
If you’re wondering if your data could have ever been leaked and if there is a risk that an unauthorized person knows your password, there is a way to verify it – visit haveibeenpwned.com. The website will allow you to check whether the e-mail or phone number you’re using has not been intercepted by thieves.
Source: haveibeenpwned.com
4. Enable two-factor authentication
Two-factor authentication (2FA) is a way to protect your account, for example, the domain administration panel, from people who may have obtained your user ID and password in an unauthorized manner. Two-factor authentication consists of an additional verification stage, i.e. entering a special code, which is sent, for example, to an external device – such as a smartphone – or to a previously assigned e-mail address.
At LetsDomains.com, we offer two-step verification via the external Google Authenticator mechanism. The process consists of generating a code with a short validity period in the smartphone application, which must be entered in the login window of the administration panel. Instructions on how to configure Google Authenticator to use with a LetsDomains.com account can be found in the administrative panel.
5. Secure the domain with Registry Lock or Registrar Lock
The Registry Lock service secures domains against unauthorized access by third parties and accidental modifications. Registry Lock will help you prevent potential attackers from, among others, changing the subscriber, transferring the domain to another registrar, or deleting it. The security measures are applied at the level of the registry (the unit that manages a given domain), thanks to which you gain effective protection against unfavorable changes being applied to your domain. At LetsDomains.com the service is available solely for .pl and .eu domains. It can be deactivated at any moment, but in the case of a .pl domain, you will need to activate it again to use it. In the case of a .eu domain, you can temporarily remove the block. In case of interesting in activating the Registry Lock, please contact us.
A similar solution is to use the Registrar Lock service. It is also a registry-level option used to prevent unauthorized or accidental domain modification. Registrar Lock is free and works for global and new domains.
It is worth noting that additionally, regardless of the registrar, the transfer lock of such domains is always imposed, regardless of the Registrar Lock service, for 60 days from the moment of registration, the last transfer or assignment, and it’s not possible to deactivate it earlier.
To check if the domain has Registrar-Lock enabled, you can use the WHOIS database, enter the domain name and search for the "Domain Status: clientTransferProhibited" entry.
6. Double-check your domain registrar and see what security conditions it offers
Don't register your domain name with the first registrar you find. Instead, read the opinions about registrars online and check what security conditions they provide.
Domain registrars should be able to provide more than just registrations, renewals, and transfers. Look for a registrar that offers complementary services such as SSL certificates and hosting. A good registrar will also allow many contact methods.
Check what formalities are required to transfer the domain. A trustworthy registrar should absolutely require additional authorization when downloading the authinfo code. At LetsDomains.com, you can get the authinfo code in the administrative panel. A reasonable compromise between safety and comfort is crucial here. Codes available directly in the panel are convenient, but they disqualify the registrar as a safe service provider. On the other hand, the procedure of issuing the authinfo code should not be associated with too complicated formalities (making it difficult to transfer the domain), such as the requirement to conduct correspondence via traditional mail.
7. Never share your login credentials and keep them private
Protect your domain administration login details the same way you protect your bank login credentials. Never share your login details with anyone. Even if you are fully protected against potential attacks from outside, you can’t be sure if the other person has taken similar precautions.

8. Keep your contact details up to date
Always make sure you’ve updated your contact details in the system, for example when you’ve changed your address, moved your office, or reassigned the administration of domains in your company to another individual. It is especially important to update your phone number and e-mail address, as this data may be used by the registrar to try to contact you if they detect suspicious activity related to your account.
What to do when an unauthorized person gains access to the domain's administration panel and, for example, changes the DNS settings?
If you notice that an unauthorized person has gained access to your domains panel, for example after verifying the last (unauthorized) time of logging into the account, immediately inform your registrar. They should know what action to take in such moments.
Change the password for your domain account, the e-mail linked to the domain panel, and, if needed, the hosting account.
At LetsDomains.com, we have developed security procedures that minimize the consequences of intrusion into your account, but you must remember to notify us about the entire incident as soon as possible.
What to do in the event of an unauthorized transfer of an internet domain?
If your domain has disappeared from your registrar's panel, it doesn't necessarily mean it has been stolen. Maybe it has expired due to an oversight or lack of payment, maybe it’s on a different account with the same registrar, or it has been suspended for some reason. Quickly contacting your registrar’s customer service will surely prove helpful.
It is worth checking the information about the domain in the WHOIS database on your own. The scope of the data provided depends on the policy of a given registry and the type of subscriber. Most often, the subscriber's data will not be available publicly. However, you’ll be able to check the expiration date of the domain and who owns it. Has the domain simply expired? If this didn’t happen, and you see an unknown registrar in the WHOIS database, contact your registrar as soon as possible.
You should find out what happened to the domain, if and when it was transferred, and how it was authorized. This information will be extremely valuable for the success of your domain recovery attempts. If your suspicions about an unauthorized transfer are confirmed, also contact the new registrar and inform them about this fact. You should try to prevent further activities on a given domain, in order to be able to clarify the doubts. At this stage, it is also worth using legal aid.
Summary – how to avoid domain theft?
Domain theft is a practice that can happen to anyone who does not follow basic security precautions. Most importantly, avoid logging in to your accounts via publicly available devices that anyone can access. Do not log into open Wi-Fi networks as they may be set up specifically to intercept sensitive data. Never send your login details to third parties.
Sometimes, despite adhering to basic security precautions, you may fall victim to frauds beyond your control, meaning a data leak on one of the platforms you’re using. Therefore, it's a good idea to use a different password for every account. Moreover, we highly recommend enabling two-step authorization, if the platform you’re using offers such an option.
Remember to update your account details, as we will use them to contact you if we notice any suspicious activity related to your domain.
If you notice that an unauthorized person has breached your domain account, please inform your registrar immediately. If your domain has been stolen, ask them for help and report the situation to the registry. You can also consider recovering your domain through the courts.
FAQ – domain theft and protection
1.What is domain theft (domain hijacking)?
Domain theft, also known as domain hijacking, is an unauthorized takeover of a domain name, usually by changing DNS settings or transferring the domain to another registrar.
2.How can I protect my domain from theft?
You can secure your domain by using strong, unique passwords, enabling two-factor authentication, avoiding public Wi-Fi, and applying Registry Lock or Registrar Lock.
3.What should I do if my domain is stolen?
Contact your registrar immediately, check WHOIS data to confirm the transfer, and request intervention. If necessary, seek legal assistance to recover the stolen domain.
4.What is Registry Lock?
Registry Lock is an advanced security service that prevents unauthorized domain transfers, deletions, or ownership changes at the registry level.
5.Is two-factor authentication really necessary for domains?
Yes. 2FA adds an extra layer of protection, making it much harder for attackers to log in to your registrar account, even if they obtain your password.
I am promoting our services, products, and software. I work closely with the development and support teams, create campaigns and content, manage social media, and translate complex technical concepts into clear communication for our customers.